Researchers at the University of Cambridge conducted a study on the sensitivity of personal data on Android after a factory reset. According to them, in January 2014, on more than 630 million Android devices, the factory reset left personal and confidential data such as photos, messages and even passwords lying around on the partitions. Bad news for all those who plan to finance their new smartphone through the resale of the old one.

When you reset an Android smartphone or tablet, you expect all of your personal data and apps to be deleted. However, this is not always the case. Last July, the Avast antivirus teams made a rather unfortunate discovery since factory resetting Android devices did not erase personal data properly. University of Cambridge researchers Lauren Simon and Ross Anderson drive home the point with a just-published 10-page study. Between January and May 2014, they purchased used Android phones to study factory restore behavior. In the vast majority of cases, personal and sensitive data was readable after the operation through tools that are not necessarily easy to use.
The Android menu allowing you to restore the factory values (here under Android Lollipop).
The study is extremely interesting since the two men have assembled a panel of 26 devices, under different versions of Android (Froyo, Gingerbread, Ice Cream Sandwich, Jelly Bean and KitKat). They were therefore able to analyze the behavior of each version of the OS, under different devices. It's very simple, almost no device reacts the same to a factory restore. For some, it is necessary to go through the Recovery (and not the Android Settings) to erase part of the personal data once and for all. For others, it is on the contrary the Phone settings that will take care of the data. And for the last category (the most numerous), the majority of sensitive data will remain in flash memory forever.
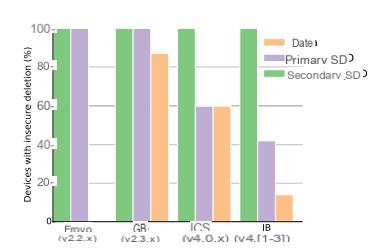
Percentage of devices with an insecure reset. Data corresponds to the data of the applications. Primary SD to personal data. Secondary SD to data stored on a physical SD card.
However, since Jelly Bean, Google foresees the possibility for manufacturers to implement a factory restore which erases the data of the / data partition containing the data of the applications. It is still necessary that the manufacturer takes this into account and integrates the necessary drivers to send the ioctl (BLKSECDISCARD) magic command to flash memory. For the / sdcard partition, which stores personal data, Google does not facilitate the work of builders. Thus, AOSP does not foresee the possibility of sending the famous command to erase this data physically. Thus, by default, they are only logically deleted (Android no longer sees them) but are still physically available, on flash memory chips. Unless the manufacturer uses an emulated / sdcard partition that is physically stored in the / data partition. In this case, the / sdcard partition will be formatted the same as the / data partition. If the manufacturer uses the correct method (physical formatting), then the two partitions will be almost unreadable for a possible hacker. Special case: Android Froyo perfectly deletes the data contained on the / data partition (as can be seen in the graphic above) thanks to the use of the Yaffs2 file system allowing direct access to flash memory chips unlike the duo FAT - eMMC used from Gingerbread.
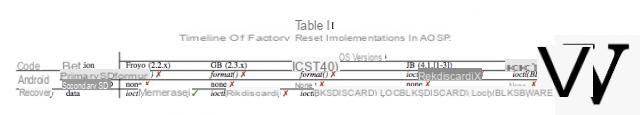
Erasure methods according to Android versions
There are, of course, methods to successfully extract information from flash memory chips that would have been properly formatted in Android, but they require special skills and equipment. In contrast, with sloppy (or rather just logical formatting) it is much easier to recover personal data (contained in / sdcard partition) and sensitive data (from the / data partition) such as Wi-Fi password or even Google account login tokens. The researchers have indeed managed to recover their own token on a terminal, to reset it, then to reinject the token to regain access to the Google account, without using any password.
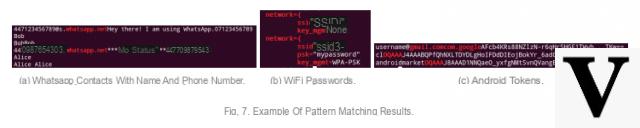
Example of recoverable data
How to properly erase your data?
The researchers then give some avenues for users to erase their personal data before separating from their terminal. This is for example the case of applications which write random data to / sdcard partition after factory restore in order to make old data that may still be physically present on the flash memory cells unreadable. But this solution is not reliable since it is not likely to work on all terminals in the same way (due to the use of different file systems and their specificities) and does not concern the / partition. sdcard. It is then possible to fill all partitions with random data, but then you need root access and to perform the manipulation from a computer connected by USB with the ADB commands. A method that has its limits when the eMMC memory controller has made use of overprovisioning and therefore sensitive data is on a flash memory cell which is no longer linked with the file system. Overprovisioning allows part of the flash memory to be used when certain cells are too worn out. However, the data remains on the spent cells and is not erased.
To read on the subject
How to really delete confidential data on Android?
Lollipop's default encryption quietly dropped
Phone encryption: a safe option?
Finally, the last solution is to encrypt your phone before performing the reset. Researchers advocateactivate encryption as soon as you start using your phone. Otherwise, clear data could be present in the flash memory cells as a result of the overprovisionning. In addition, some phones do not support partition / data encryption although AOSP provides this possibility from Jelly Bean. To add a layer, the authors specify that the encryption key is stored in the last 16 kb of the / data partition. Too bad since the end of the / data partition is the one that has the least chance of being properly formatted since no data is likely to be overwritten over it.
Work to do for Google and builders
The study therefore ends with 8 recommendations for manufacturers in order to guarantee maximum protection of sensitive data. This therefore requires the use of Google recommendations present in the source code of AOSP as well as certain tips such as sending a message to the applications before the restore to ask them to revoke their permissions or even to store the encryption key at the start of the partition in order to increase the chances of physically deleting it during a restore.
We hope that manufacturers will take this study into account and that Google will strengthen the recommendations and the possibilities offered by AOSP for the physical erasure of data. It would also be interesting to carry out the same study with newer phones and under Android 5.x Lollipop. For the more curious, the 10-page study (in English) is available for download in PDF format. Convenient for those who want to know more about the technical details of the case.